Cybersecurity
Abstract
Cybersecurity investigates how architecture can visualize, spatialize, and govern the immaterial domain of digital warfare and surveillance. Originating as an advanced studio at the Bernard and Anne Spitzer School of Architecture, the project examines the invisible infrastructures that define twenty-first century conflict—data centers, cables, servers, and algorithms—and proposes a new typology for a Cyber Security Facility in New York City. Drawing from precedents such as the Stuxnet attack on Iran’s Natanz nuclear plant, the studio explores how virtual operations produce tangible spatial and geopolitical consequences. Through research with journalists, legal experts, and cyber-industry partners, the study tests how architecture can mediate between protection and exposure, secrecy and transparency, individual rights and collective safety. The project situates cyber security as a spatial question: how to give physical form to systems whose operations are distributed, borderless, and often unseen.
Context
The late 2010s marked a pivotal moment in the recognition of cyberspace as both a battlefield and a civic arena. The Stuxnet malware, discovered in 2010 at Iran’s Natanz nuclear facility, demonstrated how digital code could inflict physical damage on industrial equipment. In doing so, it collapsed the division between virtual and material space. This precedent exposed the city, the factory, and the network as interlinked infrastructures—each capable of transmitting conflict across domains.
In parallel, the expansion of global data networks redefined the concept of territory. Submarine cables trace the old geographies of empire; cloud computing redistributes sovereignty into private hands. Every phone, server, and satellite extends the city’s operational footprint beyond its borders. As Edward Snowden’s disclosures revealed, this system of total interconnection also enables total surveillance. The question of safety becomes inseparable from that of trust: who holds data, and under what authority?
The studio situates these dilemmas within the urban and institutional fabric of New York City—a financial and media capital where digital infrastructure underpins nearly all operations. The New York City Economic Development Corporation’s “Cyber NYC” initiative, launched in 2018, framed cybersecurity as a driver of economic growth and civic resilience. Yet its physical dimension remained undefined. What does a building dedicated to defending the digital realm look like? How does it express a program that must remain partly hidden?
The research positions cybersecurity not only as technological but as architectural: an ethics of visibility and access. Its physical manifestations—server rooms, data vaults, secure meeting spaces—exist in tension with demands for transparency and collaboration. The cyber facility becomes both shield and interface, a material mediator between secrecy and public trust. The studio thus redefines security architecture as an urban agent that extends beyond its own walls through networks of connection, monitoring, and exchange.
Methods
The project proceeds through investigative mapping, typological analysis, and speculative design. Each phase builds on a series of assignments structured to translate the virtual logic of networks into spatial and architectural reasoning.
1. Mapping Territories Under Threat.
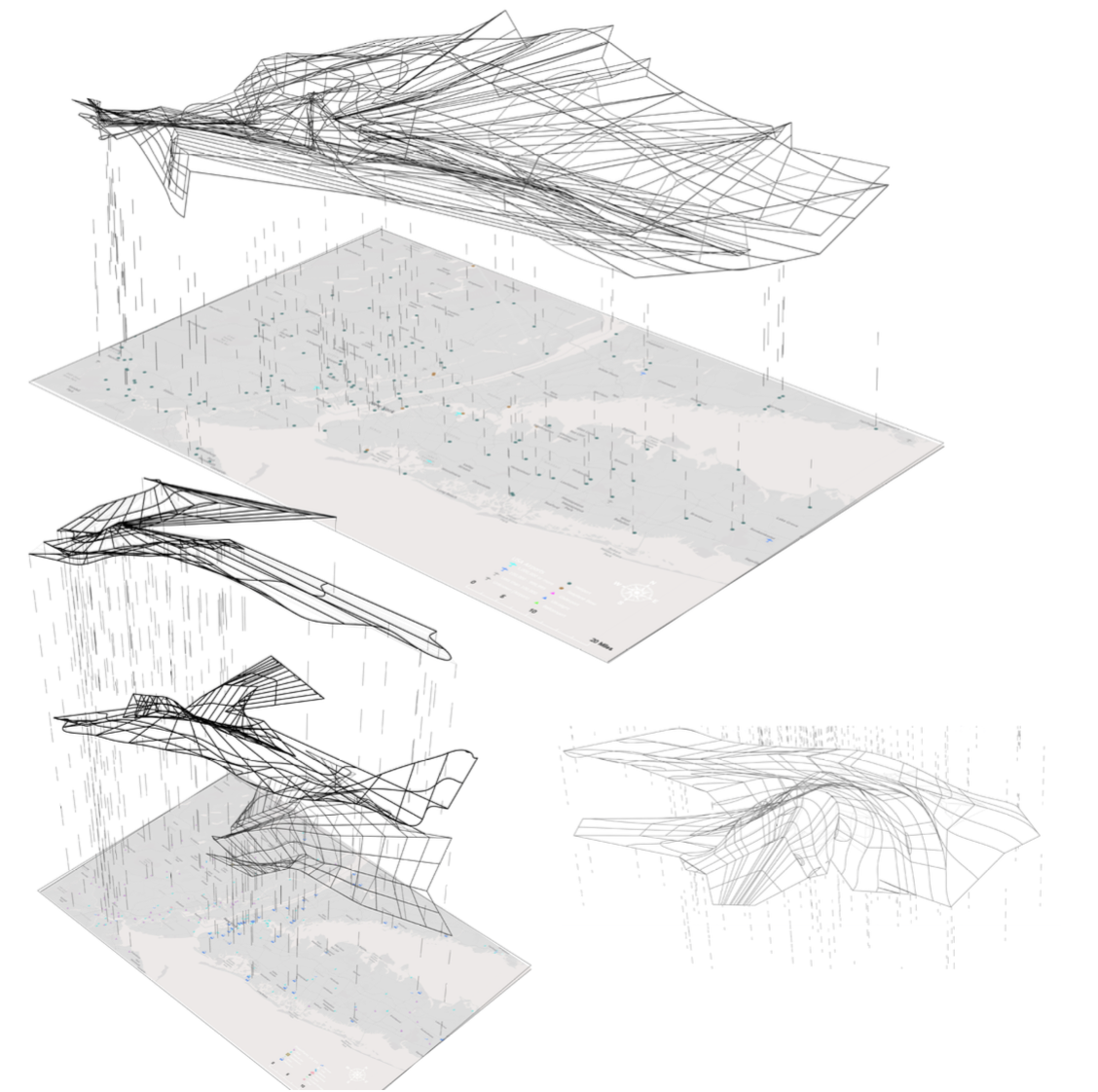
Students mapped layers of vulnerability across scales—from global fiber-optic routes and satellite paths to local data centers, hospitals, and transit systems. These maps exposed how digital and physical infrastructures overlap. Cyberattacks on critical systems—finance, energy, transportation—were diagrammed as circulations of risk. The exercise revealed that the building’s agency extends beyond its plot; it operates as a node within a dispersed field of defense.
2. Functional Program Development.
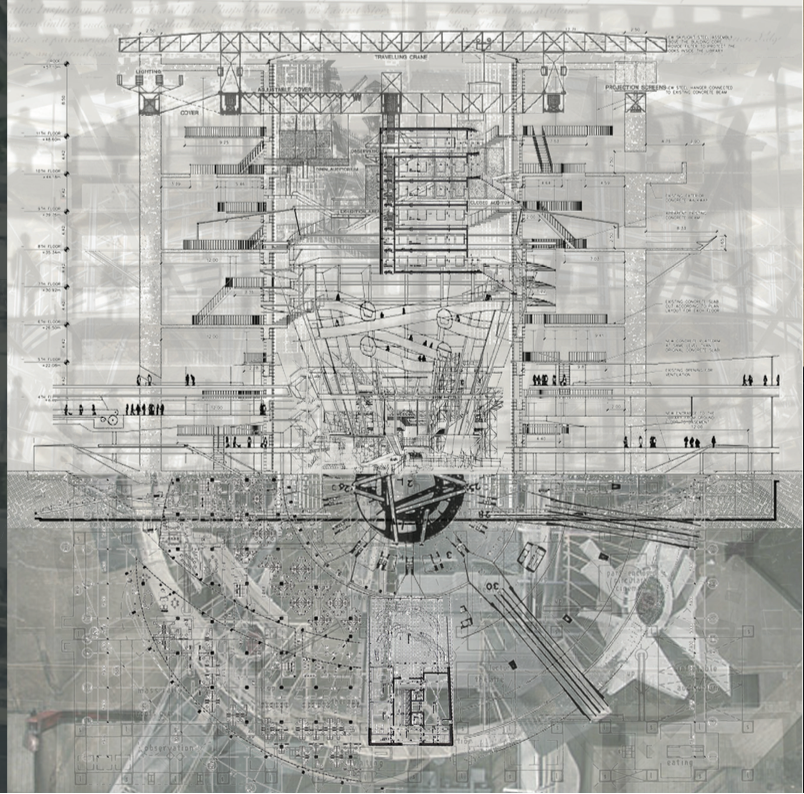
Based on these mappings, the class articulated a spatial program for a prototype Cyber Security Facility. The 20,000-square-foot program included server farms, “cyber ranges” for simulation training, forensic labs, offices, and an exhibition component termed the “Cyber Museum.” Each space corresponded to a layer of interaction—local, regional, national, and global—reflecting the nested nature of digital systems. Cable pathways, firewall rooms, and secure circulation were treated as generators of form.
3. Typological Research.
Precedents such as SOM’s 911 Call Center, Herzog & de Meuron’s Signal Box, and Erick van Egeraat’s Roskilde Waste-to-Energy Plant were analyzed for their handling of security, transparency, and public interface. These studies informed an understanding of architecture as both infrastructural and symbolic—an interface between trust and power.
4. Site and Material Investigation.
A traffic island near Manhattan’s Holland Tunnel was identified as the test site—an exposed, infrastructurally charged location symbolizing both connection and vulnerability. Its isolation offered security advantages while foregrounding visibility. Material investigations explored composites of glass, concrete, and conductive metals to suggest both opacity and transmission.
5. Iterative Design and Simulation.
Digital modeling and physical prototyping tested how enclosure systems could express degrees of access. Parametric studies examined airflow and cabling pathways as aesthetic and organizational devices. Visualization tools borrowed from data analytics—network diagrams, heat maps, and latency charts—were reinterpreted as architectural drawings.
Across these methods, the studio treated architecture as a diagnostic instrument: revealing invisible systems through spatial reasoning.
Findings / Reflection
1. Architecture as System Interface.
The design process redefined the building not as a static enclosure but as an interface linking multiple systems—human, digital, infrastructural. Walls and floors are conceived as membranes for data, sound, and energy flow. The building’s geometry follows network logic rather than classical order: redundant paths, compartmentalized circuits, and layered access zones correspond to protocols of cybersecurity such as segmentation, redundancy, and isolation.
2. Typology of the Invisible.
A central question emerged: how to visualize a typology whose function depends on invisibility. Traditional architectures of defense express power through opacity; contemporary cyber defense requires controlled transparency. The proposal articulates this duality through material gradation—perforated cladding, filtered glass, and light-responsive skins—allowing partial glimpses of activity while maintaining security. The architecture communicates trust without revealing its code.
3. The Cyber Museum.
An unexpected outcome was the integration of a public exhibition component within a secure environment. The “Cyber Museum” bridges two contradictory imperatives: public education and system protection. Visitors move through controlled zones that narrate the history of digital warfare—from Stuxnet to Cambridge Analytica—while adjacent data labs remain sealed. This juxtaposition translates the ethics of transparency into physical experience: knowledge and protection coexist through calibrated thresholds.
4. Governance and Protocols.
Design research identified governance as an architectural parameter. The building embodies layered authorization systems—public lobby, controlled research areas, classified chambers—each corresponding to digital access levels. The architecture therefore materializes policy: trust becomes spatially encoded. This approach parallels ideas from Keller Easterling’s Active Form, where spatial arrangements carry regulatory power.
5. From Defense to Ethics.
Cybersecurity extends beyond defense against attacks; it mediates fundamental questions of privacy, autonomy, and surveillance. The facility’s dual purpose—protection and exposure—reflects this ethical tension. By spatializing the flow of information, architecture can reveal the balance between individual rights and collective security. The building’s circulation paths, sightlines, and material transitions mirror the logic of firewalls and encryption—limiting visibility while ensuring functionality.
6. Global Network Awareness.
Mapping exercises revealed that each local node participates in global systems of communication, finance, and defense. Submarine cable routes, cellular towers, and data centers form a distributed urban morphology that transcends national borders. The Cyber Security Facility thus operates as a geopolitical agent: a microcosm of digital sovereignty. The architecture’s reach extends through invisible infrastructures to territories far beyond New York.
7. Education and Simulation.
The concept of the “cyber range”—a simulated environment for training and testing—introduces a temporal dimension. Architecture becomes a space of rehearsal rather than permanence. The studio proposes flexible interiors equipped with projection surfaces, reconfigurable cabling, and adaptive lighting to host real-time threat simulations. This adaptability positions the building as both a tool and a laboratory for evolving risks.
8. Ethical Aesthetics.
The project confronts the paradox that the aesthetics of security often mirror those of control. To avoid reproducing authoritarian imagery, the design emphasizes legibility over spectacle. Circulation ramps and bridges expose the process of movement; mechanical systems are partly revealed; the building glows softly at night, symbolizing vigilance without intimidation. The aim is to visualize accountability in an era of algorithmic opacity.
9. Broader Implications.
Cyber Security redefines architectural agency in the digital age. As cities become data-dependent, the boundaries between building, network, and user dissolve. Future architectures of governance must address hybrid threats—climate, data, health, and misinformation—through systemic design thinking. The studio’s speculative typology offers a prototype for civic infrastructure capable of hosting these negotiations.
Ultimately, the project suggests that architecture can no longer separate physical form from digital ethics. The discipline must engage with protocols, encryption, and data governance as design materials. Cyber Security transforms architecture from a backdrop of technology into an active participant in shaping how societies define safety, freedom, and trust.
Credits
Architecture Field Lab Research Program; Naomi Ben-Haim, Liza Otto, Yoo Jin Jang, Danica Lora Masiglat, Sayem Shah, Matthew Morgan, Tanha Tabassum, Daniela Polo, Christian Coronel, Jose Rafael Ruiz Noriega, Carey Baldwin, Joseph Amodeo
Collaborators: Bernard & Anne Spitzer School of Architecture (CCNY), Raphael Satter (Reuters), Alexander Urbelis (Cyberlaw), Adam Turnbull (Ethics in Internet Security)
Location: New York City
Year: 2019
Contact: info@studiostigsgaard.com